We are launching a series of blog posts about basic IoT security challenges and how to overcome them using Rust.
While hacking a computer would result in certain more or less important data being lost, hacking IoT devices can have serious material damages. Imagine a smart heater being controlled while the user is not at home or a door lock remotely opened by burglars. And these are just a few examples.
Quick Facts
To make a case of why IoT security is important, we will cover three main subjects. Click one of the links below to jump to a more detailed description.
Why is IoT security so important
The Internet of Things has become more and more common these days. Most of the devices that we use today are connected, in a way or another, to the Internet. While this allows devices to become smart and provide us with enhanced functionalities, connecting them to the Internet poses a security risk. Hacking connected devices can have serious material damages like starting a fire in your house or open the house's doors. If you think these things are a problem, brace yourselves, here are some serious IoT hacks that might have had a much worse impact.
Stuxnet###
How to damage a nuclear facility that is not even connected to the Internet
Back in 2010, this hack destroyed part of the Iranian nuclear centrifuges. This was the first time in history that a hack had material consequences. Now imagine if this hack were deployed to a nuclear power plant.
Mirai
How to make your own cloud using everyone's devices
Used in 2016, this piece of software would infect Linux devices and turn them into computing power nodes ready to be hired on the dark web. In other words, hackers have built a cloud infrastructure, just that instead of buying servers, they used hacked consumer devices. The owners had no idea of what their devices were doing in the background. Well, would you know that your hacked fridge was mining bitcoins as a side job? Probably not.
This hack was used for:
- bringing down Facebook, Amazon, GitHub, Twitter, Netflix, Airbnb, Ars Technica, OVH, and many others (DDoS attack to their DNS service);
- shut down the Internet at Rutgers University;
- try to attack Liberia's Internet infrastructure.
This attack still works today.
Why did this work? Most of the attacked devices were using default usernames and passwords. Most probably, many of them still do.
Did you change the default password for your Internet router?
WannaCry
How to shut down the NHS, a few factories, telecommunications companies, and some means of transportation
This hack is on the shortlist of being the most impactful. In simple words, it would infect a computer, encrypt its hard drive and ask for a ransom (ergo the name Ransomware). Now, this is not something new, and its impact should have been just a few lost documents. Right? So wrong! Remember computers now run almost all electronic equipment, including medical devices, network switches and routers, or welding robots. So, if such a device has its computer hard drive encrypted, it does not work anymore.
The outcome, in May 2017:
- NHS was unable to use a lot of medical equipment;
- Nissan was left without working welding and assembly robots;
- Renault stopped its production to prevent what happened to Nissan;
- Telefonica was affected;
- FedEx and Deutsche Bank were affected.
How did this happen? The hack used a Windows XP exploit. Yes, a version of Windows that was not supported anymore at that time. A lot of industrial equipment was using Windows XP, as manufacturers never understood that an upgrade is required. The systems were working perfectly.
Now imagine the damage if the target would have been critical infrastructure like power plants? It would have been the target as well, weren't for a kill switch in the hack that stopped it.
The Jeep Attack
How to remotely kill a Jeep on the Highway
Automotive manufacturers were so eager to embrace the IoT revolution that they connected their cars to the Internet. This has led in 2015 to the possibility of remotely stopping a car on the highway.
Hackers were able to remotely:
- stop the engine;
- control the infotainment;
- control steering and braking at low speeds.
This was like buying a remote-controlled toy car, but with a real one.
The Mercedes Attack
The Jeep reloaded, version 2020
Five years after the Jeep attack, the same thing happened to Mercedes.
Device security is really important
These are just a few of a large number of device hacks that we have witnessed from the beginning of the IoT industry. Security is important as nowadays the damages are not limited to software, but might have serious material damage.
IoT Security Risks
When it comes to IoT security risks, we have found out that these can be divided into three categories:
- Development Platform Security is related to the development platform used for the software that runs on devices and the cloud system;
- Networking Security is related to communication protocols used;
- Policy Security is related to the security policy that a manufacturer implements.
Now let's discuss all of them in detail.
Development Platform Security
These security flaws are related to how the application source code was written.
When developing applications, software designers have the following tradeoff: use a programming language that is secure but runs slower and consumes a fair amount of resources, or use a faster programming language when it comes to performance, but it offers fewer security guarantees. In other words, use Java or Python, but have slower and more power-consuming software, or use C or C++, but make devices less secure. Moreover, developers using low power devices, like sensors that need to run several years using a single battery charge may only use C or C++.
And there's more. Most languages like Python or Java rely heavily on native libraries written in C/C++. So even though the language offers security guarantees, its libraries are still vulnerable.
Looking through our examples, Stuxnet used a Windows library issue (written in C/C++), WannaCry used a Windows networking stack issue (written in C/C++) and the Jeep hack used a flaw in the vehicle's ECU (Electronic Control Unit) software, as you probably guessed, written in C or C++.
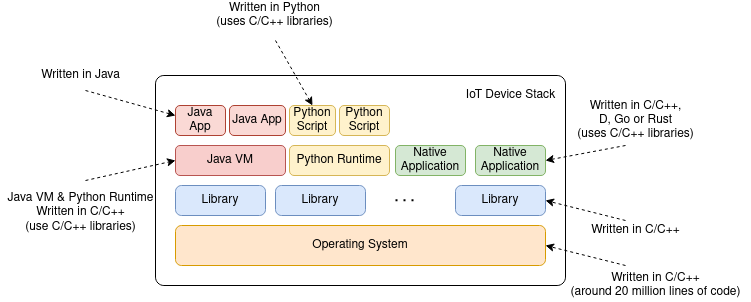
If we take a glance at how the software stack looks like for an IoT device, a pattern emerges: C/C++. The operating system, a piece of software that has around 20 million lines of code, the main libraries, the virtual machines (Java, Python, etc) are all written in C/C++. Now don't get the wrong idea, they are written by professional developers with a lot of experience, so in theory, they should be safe. Still, when it comes to millions of lines of code, there will be a mistake.
Just take a look at the following source:
int values[10];
// ...
int n = get_a_position ();
values[n] = get_a_value ();
The problem is: if n, that is obtained somehow, is larger than 9 (there are 10 positions, starting at 0 up to 9) the software will have undefined behavior as it writes that value somewhere in memory outside of the array. This can be avoided using a simple if. Now in a million lines of code source code, these errors pop up even for the most experienced developer.
C or C++ are great languages, stable, robust, the only solution at the time that they were designed; nowadays it's like driving a diesel in the era of the electric car.
We will discuss several examples in the next parts of this series.
Network Security
As devices are connected, they need a language to talk to each other. This is what we call a protocol. What started as simple data exchange protocols, at the beginning of the Internet era, has now evolved into standards that are hundreds of pages long. Protocols like HTTP, MQTT, and CoAP that are considered to be pretty simple, have already a few hundreds of pages. When it comes to things more serious such as the EMV (Europay, Mastercard, Visa) we are talking about thousands of pages.
These protocols usually stack one on top of the other. For instance, HTTP or MQTT use the underlying protocols TCP or UDP on top of IP to send and receive data.
Security issues arise from the fact that two pieces of software exchange data, but due to some error, they do not both understand the same thing. One thinks the other has requested or will do something different. The WannaCry hack relied on a mistake in the Windows File Sharing protocol (SMB).
As the IoT ecosystem is very diverse, there is not much that can be done to simplify these protocols. Our take is that once the ecosystem Stabilizes. Hopefully, devices will be less heterogeneous when it comes to software and communication and simpler protocols may be used.
What can be done though, is to mitigate the risks in software development by limiting what an application can do through the minimum access policy. This means that an app has only the rights that it actually needs. For instance, if we have an app that provides some local device services, it should never have access to the network resources.
Smartphones try to implement this by asking the user for several permissions.
Policy Security
This might be one of the most important but underrated security categories. While the previous two are technical and related to the Development and IT department, this one is related to business decisions. IoT brings a major shift in the lifecycle of a product.
Software used by appliances was uploaded to the device during the manufacturing process and was designed to stay there for the whole device lifecycle. No-one would have access to it. Devices either did not have any debugging ports exposed or one would need specialized hardware to interact with the debugging port. This changes when it comes to connected devices. Despite all the benefits that an Internet connection adds to the device, it opens up a way for others to interact with the software on the device. Any hacker now has the opportunity to hack millions of devices.
How do we improve IoT security?
What can we engineers do? Well, as far as policy is concerned, we need to raise awareness and present several arguments to management. The best advice is to read about security issues and understand why they happen and how policy decisions contribute to them.
Networking is a subject that we can handle a little better. Try to use open standards as these have been reviewed by a lot of other developers.
Software development is where we can make a real difference and this is what we mainly tackle in this series. Languages like C/C++ should have been long deprecated, but there was no real replacement for it. Now we have a very strong alternative that is Rust. Rust seems to have all the benefits of high-level languages like Java and Python while providing the level of performance of low-level languages. However, it has a steep learning curve.
There are two ways for implementing Rust in IoT:
- The Rust Embedded Workgroup Group has made an effort to provide a set of standard libraries for IoT Device Development. This is what developers usually call bare metal development;
- Tock an embedded operating system fully written in Rust and used by brands like Google and Western Digital.
The game-changer that Rust brings to the table is safe memory management. About 70% of the security issues were due to memory management (Chrome, Microsoft). Using Rust would make most of these issues impossible at compile-time, way before they reach into production software.
With this series, we aim to provide an introduction to using Rust to avoid security issues.